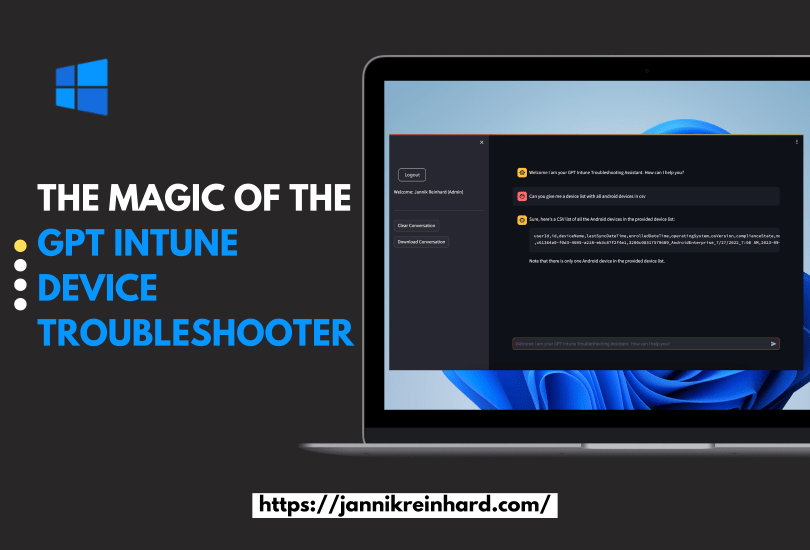
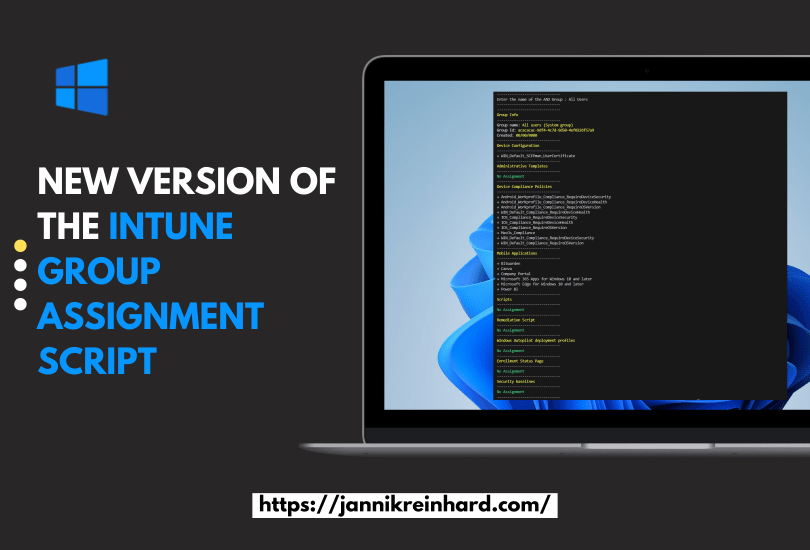
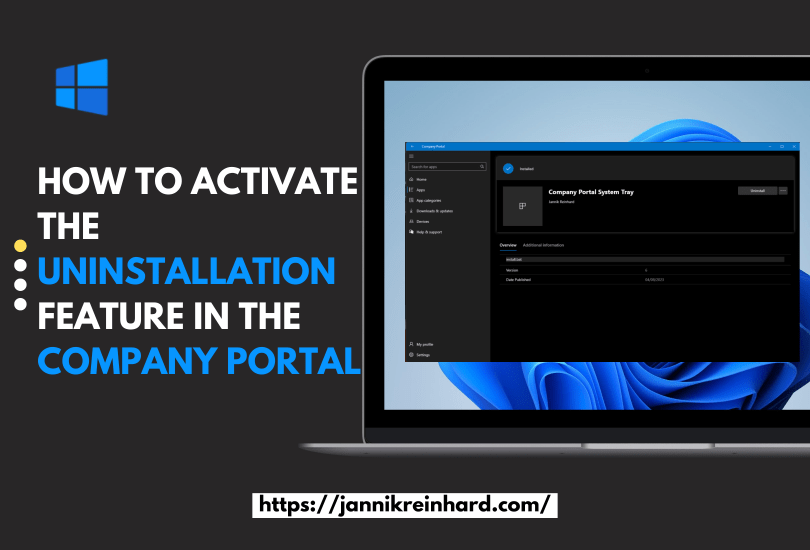
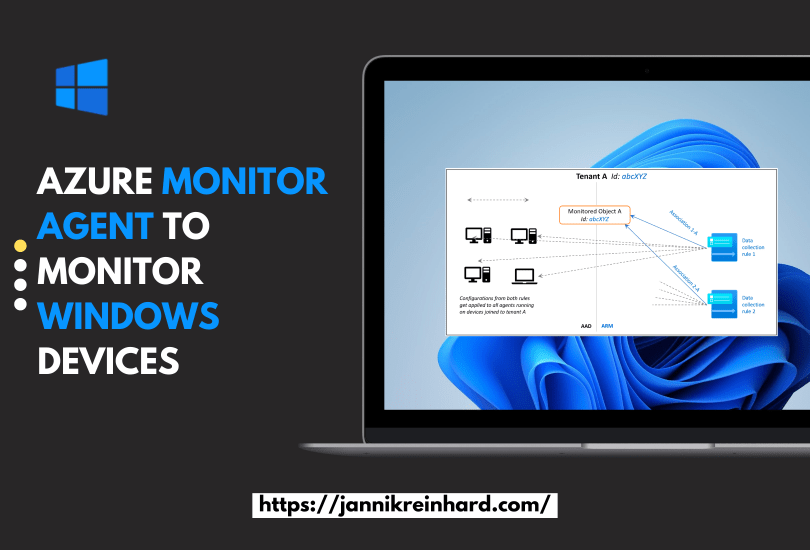
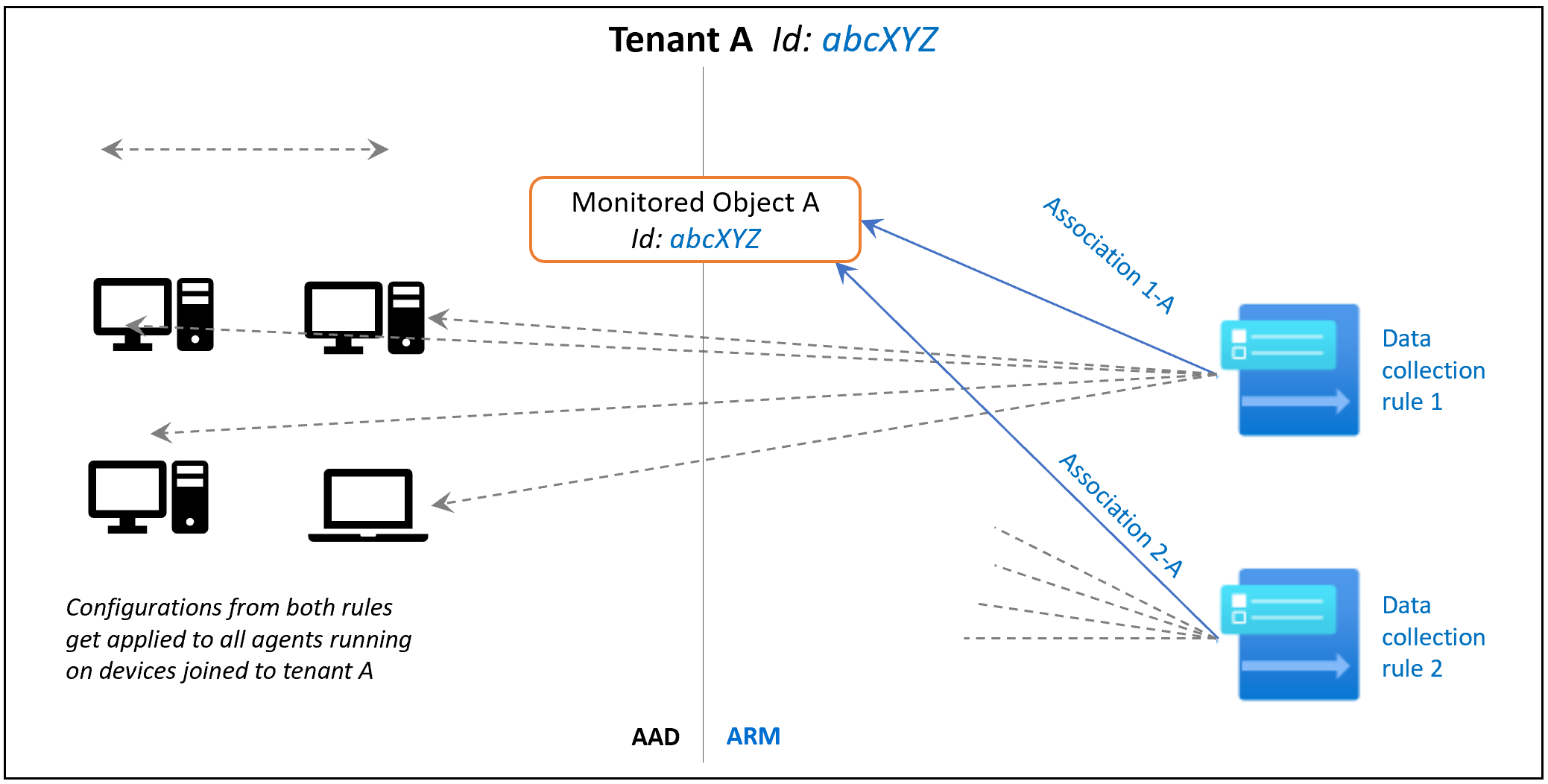
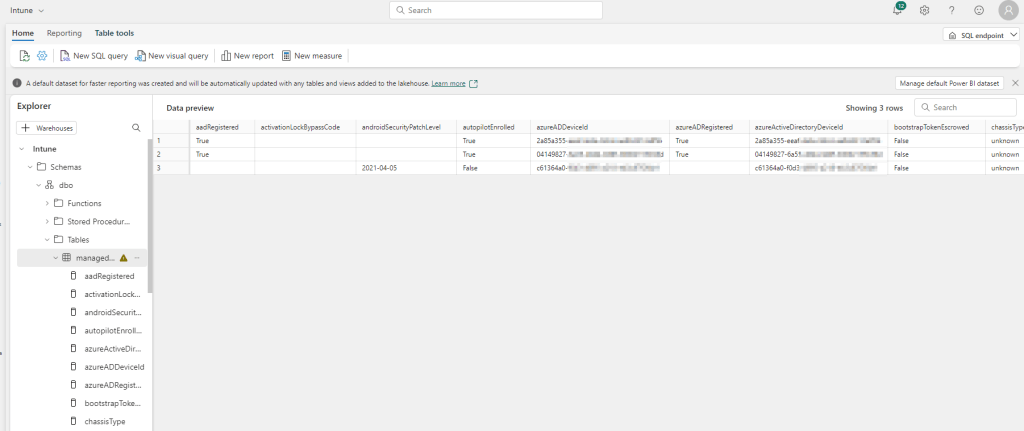
After some weeks here is the second part of my series on Microsoft Defender for Endpoint. In this pert, we delve into essential insights and best practices for Microsoft Defender for Endpoint. I will guide you through important configurations and strategies to enhance your organisations security.
Part 1 (How to enroll device to Microsoft Defender for Endpoint and how does it work)
Read More »