Endpoint management has come a long way from the days of manual, on-premises processes. In today’s world where employees work from home, on the road, or in branch offices—IT teams need tools that are not only powerful but also flexible and intelligent. Microsoft’s journey from Configuration Manager (SCCM) to Intune, and now toward AI-driven automation, shows how we can bridge legacy systems with cloud innovation to deliver seamless, secure, and proactive device management.
The Evolution of Endpoint Management
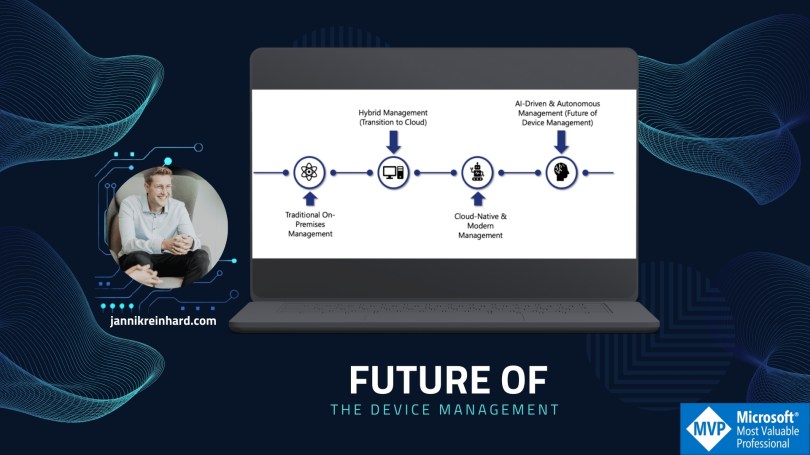
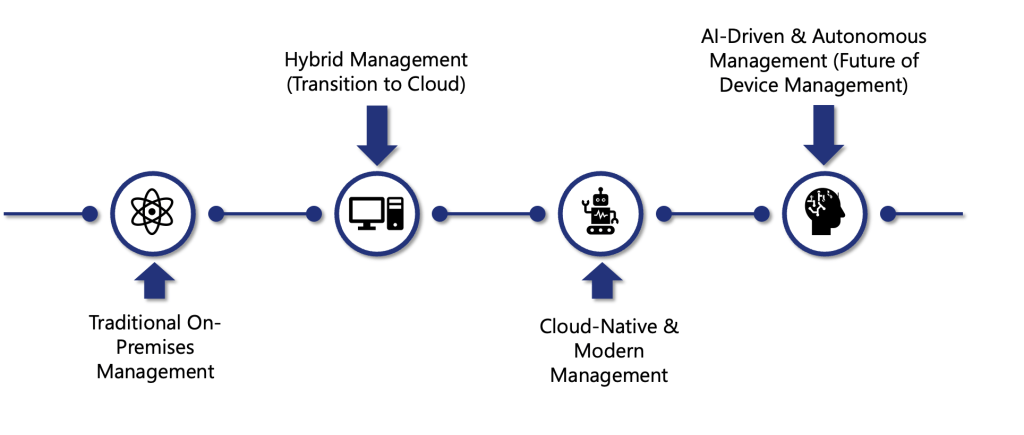
1. Traditional On-Premises Management
In the past, enterprises relied on Configuration Manager to deploy software, enforce policies, and report on device health. While robust, this model was inherently siloed: every change required manual configuration on-premise servers, and IT bore the full operational burden—resulting in high effort, slow response times, and limited scalability.
2. Hybrid Management (Transition to Cloud)
The next step was hybrid management, where organizations paired their existing SCCM infrastructure with Intune’s cloud capabilities. This blended approach allowed teams to enroll devices in Intune while still leveraging their on-prem investments. Although this introduced some complexity—managing two control planes—it provided a clear migration path and began to unlock cloud-scale benefits.
3. Cloud-Native & Modern Management
Moving fully to the cloud removes the last barriers: no more infrastructure patches, global reach for remote and hybrid workforces, and out-of-the-box integration with Microsoft 365 and Azure services. Intune brings unified endpoint management across Windows, macOS, iOS, Android, and more, all under a Zero Trust security model.

Why to move to modern management?
Modern device management isn’t just about scale—it’s about speed, security, and user experience:
- Efficiency & Scalability: Automate routine tasks to free IT from manual scripting.
- Global Reach: Manage devices wherever they are, without VPN backhauls.
- Security First: Enforce policies by default, detect threats in real time, and respond instantly.
- Unified Management: One console for all platforms, with built-in reporting and compliance.
- Zero Trust: Continuous evaluation of device health and user behavior to minimize risk.
Embracing AI-Driven & Autonomous Management
The future lies in shifting from reactive firefighting to proactive prevention:
- From Reactive to Proactive
Machine learning models can predict failures or security incidents before they happen—allowing IT to resolve issues during off-peak hours and keep end users productive. - Intelligent Automation
By codifying routine maintenance (patching, remediation scripts, policy enforcement) into automated runbooks, teams reduce human error and accelerate service delivery. - Decision Support
AI-powered analytics sift through telemetry and usage data, surfacing recommendations (e.g., retire legacy configurations, tighten security baselines) so administrators can make informed, data-driven choices. - Personalized Experiences
Tailor device configurations to different user personas—high-security profiles for executives, flexible policies for contractors—without re-engineering entire management frameworks. - AI as Co-Pilot, Not Replacement
Automation handles the “busy work,” while IT professionals focus on strategy, policy, and the critical decisions that require human judgment. Continuous learning loops between AI and IT pros ensure both get better over time, and new roles emerge around AI training and oversight.
Key Technologies in the Modern Stack

As organizations embrace cloud-native endpoint management, four core technology pillars provide the foundation for a secure, scalable, and intelligent future. Let’s dive into how Security, Data, Automation, and AI work together to form today’s modern device-management stack.
1. Security: Zero Trust by Default
Modern endpoint management isn’t complete without a robust security posture baked in. Under a Zero Trust approach, every device and user must continually prove their identity and health before being granted access:
- Conditional Access Policies evaluate real-time signals—device compliance, user risk level, network location—and dynamically grant or block access to corporate resources.
- Endpoint Detection & Response (EDR) continuously monitors device behavior for anomalies (unusual processes, lateral-movement attempts) and can automatically quarantine or remediate compromised endpoints.
- Built-in Encryption & Patch Management ensure that devices are always running the latest security updates and that data at rest or in transit remains protected using industry-standard algorithms.
2. Data: The Fuel for Insight
In the ai and cloud era, telemetry is king. Comprehensive, high-fidelity data from endpoints powers both reactive troubleshooting and proactive optimization:
- Device & Application Telemetry streams performance metrics (boot times, app launch durations, CPU/memory utilization) back to centralized analytics engines.
- Compliance & Configuration Audits catalog every registry setting, policy assignment, and software inventory across your estate—enabling rapid reporting and targeted remediation.
- User-Experience Analytics captures network latency, and crash data, helping you pinpoint the true pain points in your digital workplace.
When you aggregate this data in a unified data lake (e.g., Azure Data Explorer or Log Analytics), you unlock deep historical trends, powerful ad-hoc queries, and the ability to feed automated playbooks or machine-learning models.
3. Automation: Scale with Consistency
The sheer volume of devices—coupled with frequent OS updates, ever-evolving threat vectors, and diverse form factors—makes manual management untenable. Automation bridges that gap:
- Proactive Remediation Scripts run on a schedule (or in response to alerts), automatically fixing known issues like stalled Windows Update services or misconfigured firewall rules.
- Azure Automation & Runbooks orchestrate complex, cross-platform processes without human intervention.
By codifying best practices into repeatable automation pipelines, IT teams shift from firefighting to innovation, delivering consistent outcomes at cloud scale.
4. AI: Turning Data into Decisions
Automation excels at executing known tasks, but AI elevates your stack by predicting, prescribing, and personalizing:
- Predictive Maintenance models analyze historical telemetry to forecast which devices are likely to fail or require intervention—so you can remediate before users even notice a problem.
- Recommendation Engines surface configuration tweaks (e.g., retiring legacy GPOs, tightening compliance baselines) tailored to your estate’s unique usage patterns.
- Natural-Language Interfaces (chatbots or copilot integrations) let administrators query device health, generate reports, or trigger runbooks via simple conversational prompts.
Rather than replacing IT pros, AI acts as a co-pilot—amplifying human expertise with data-driven insight, accelerating root-cause analysis, and continuously learning from each interaction.
Bringing It All Together
When security, data, automation, and AI converge in a unified, cloud-native stack, endpoint management transforms from a reactive chore into a proactive, strategic advantage. You gain near real-time visibility, iron-clad protection, and the agility to adapt to new challenges—all while liberating your team to focus on innovation rather than administration. That is the promise of modern device management.
Preparing Your Organization
- Start Small, Grow Big
Pilot a single scenario—such as automated patch remediation—then expand once you’ve proven ROI. - Ensure Data Quality & Security
Accurate device data is the foundation of reliable automation and threat detection. - Upskill Your Team
Provide training on Intune fundamentals and core AI concepts to build trust and reduce resistance. - Iterate & Improve
Collect feedback, refine your runbooks, and tune AI models to better align with your environment’s unique needs.
Key Takeaways
- AI & Automation Are Game-Changers: They boost responsiveness, reduce toil, and elevate IT’s strategic impact.
- Microsoft Has the Building Blocks: From Graph APIs to proactive remediations, most capabilities are ready to use today—so don’t wait!
- People Still Matter: Human oversight, policy definition, and continual improvement remain at the heart of successful endpoint management.
By following this roadmap—evolving from on-premises to AI-driven autonomy—organizations can not only keep pace with today’s security threats and hybrid work models but also unlock new levels of efficiency and insight. Now is the time to embrace the future of device management.